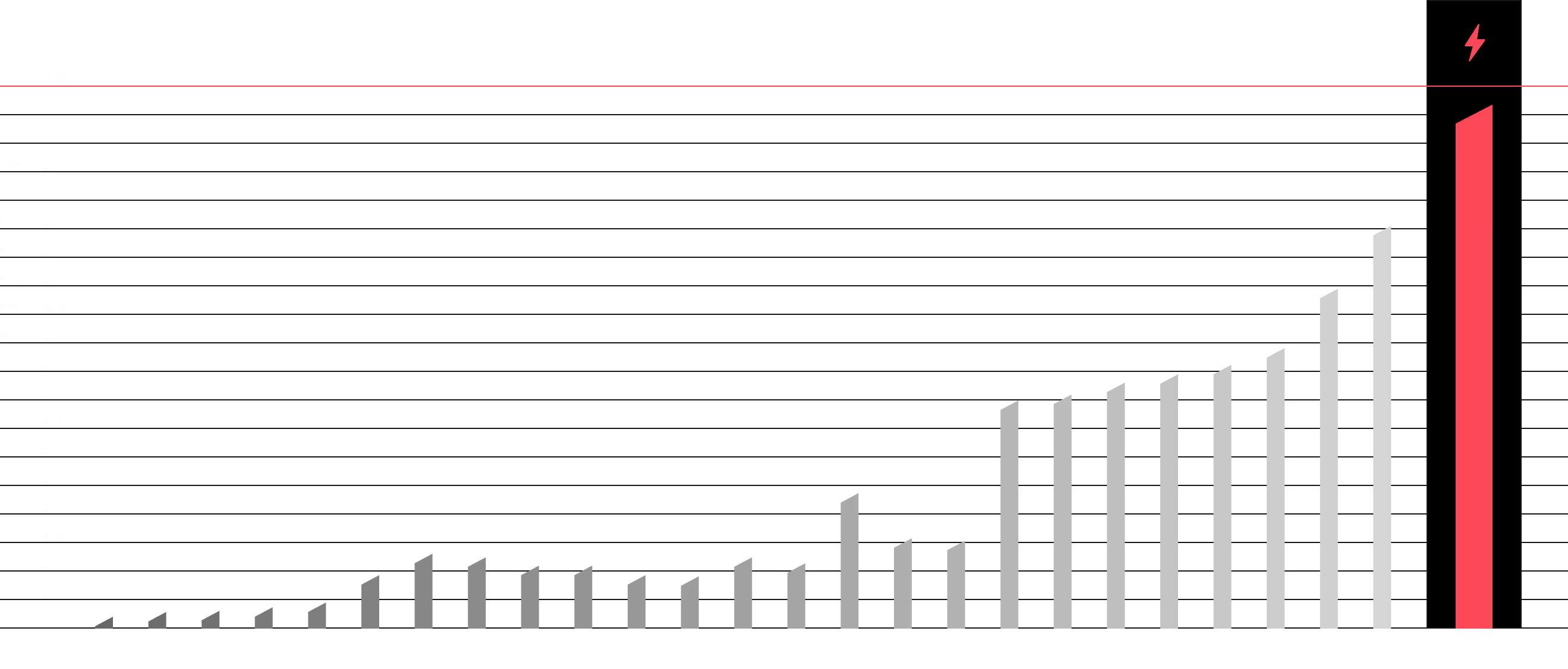
For Management and the C-Suite we prepare a strategic management dashboard. It presents key metrics, such as the overall company Risk Score, trends in the emergence of new vulnerabilities, and the most common attack vectors. This "bird's-eye view" allows for a quick situation assessment and the making of informed business decisions, supported by analyses from our Fuse AI technology.
For the IT Team and Engineers each vulnerability is a specific, actionable task. Our system integrates with platforms such as Jira, automatically creating tickets that contain a detailed technical description, precise remediation recommendations, and assigned priorities and SLAs. It's an operational view that turns analysis into action.