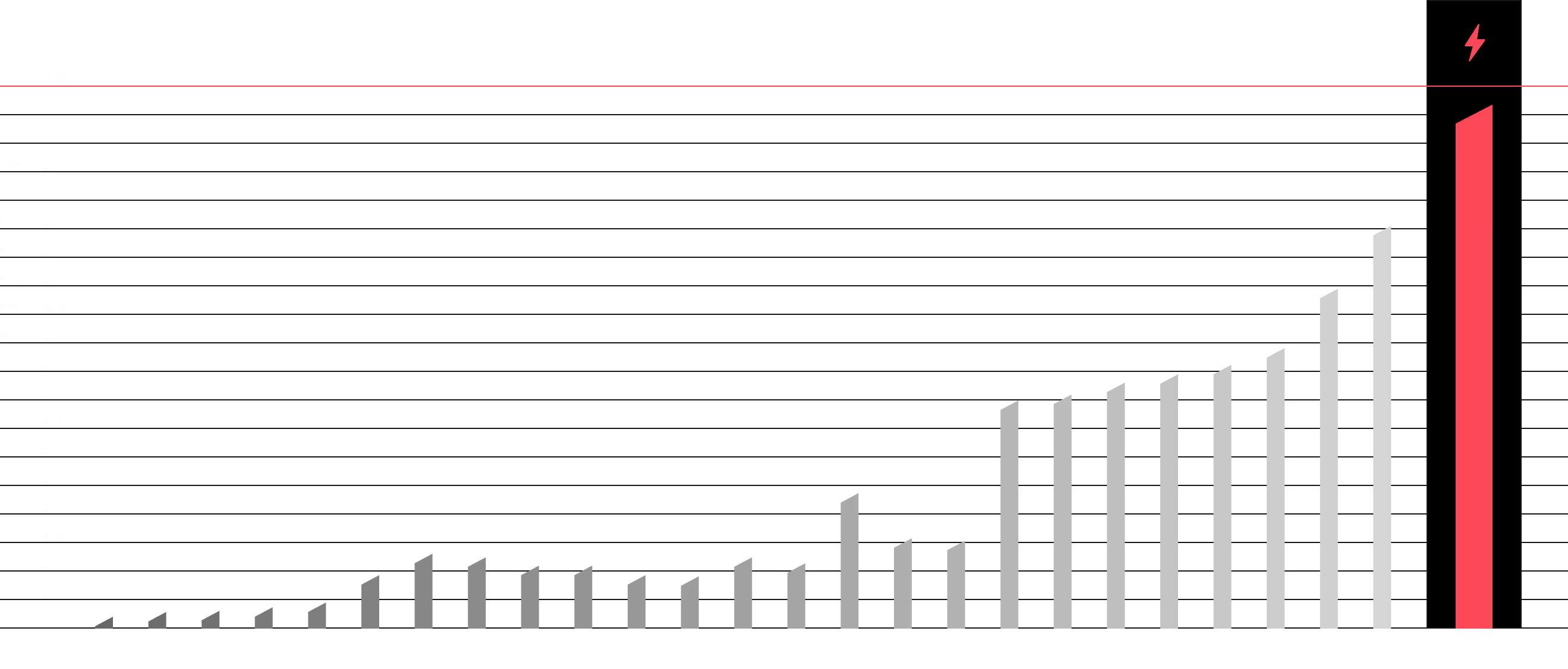
However 90% of the iceberg is under water. This is your hidden attack surface — vast, uncontrolled, and invisible to you, but perfectly visible to attackers. This is where data leaks, unsecured assets, and information that allows them to bypass your main fortifications are located.
Our OSINT Analyst is like a military sonar. We map your full, underwater attack surface, giving you a chance to defend it before it becomes an entry point for the enemy.