raining
Arm Your Team With the Most Effective Weapon: Knowledge.
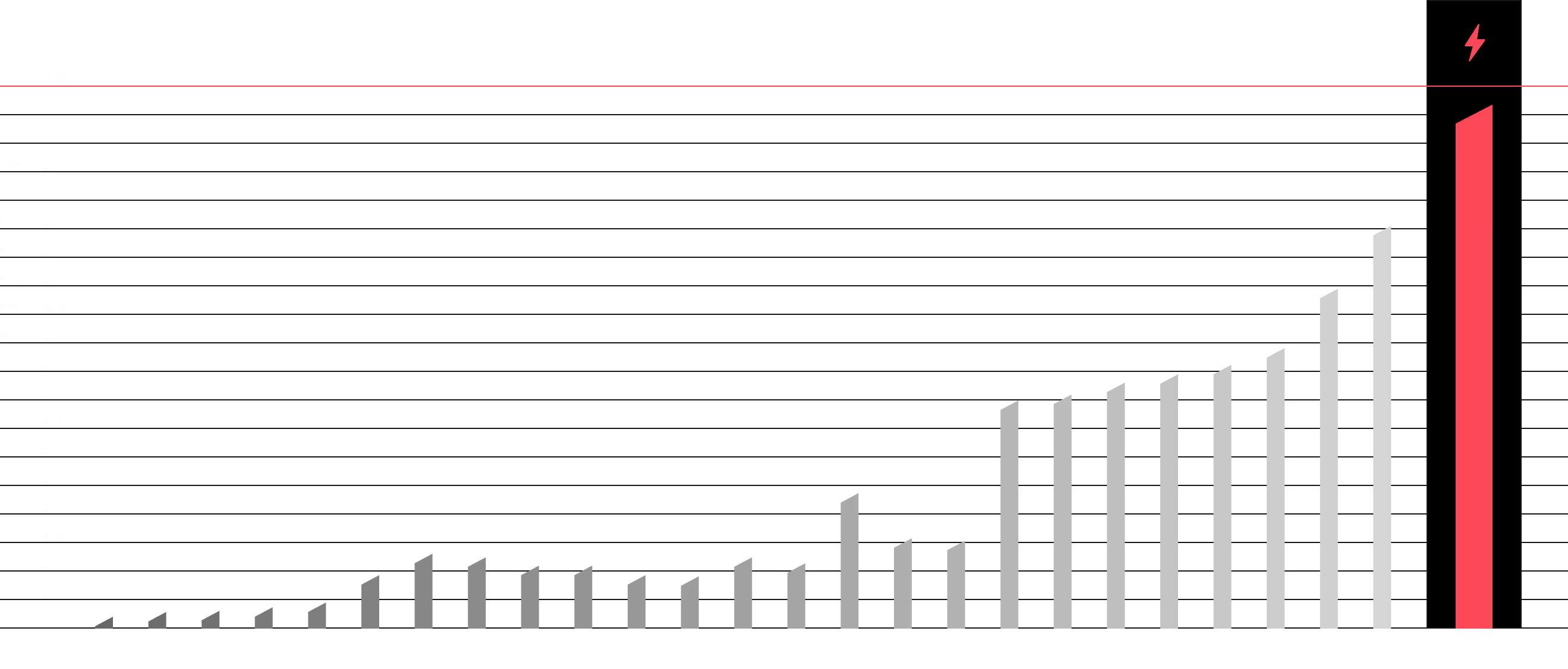
In the digital world, knowledge is the most powerful weapon. Attackers exploit its lack to break through defenses, but we reverse that. Our training programs — from hands-on workshops for technicians to strategic sessions for the board — arm your team with the knowledge to not only react but also to anticipate threats.
Overview