AI SECURITY & TRUST
Your AI is intelligent.
But is it obedient?
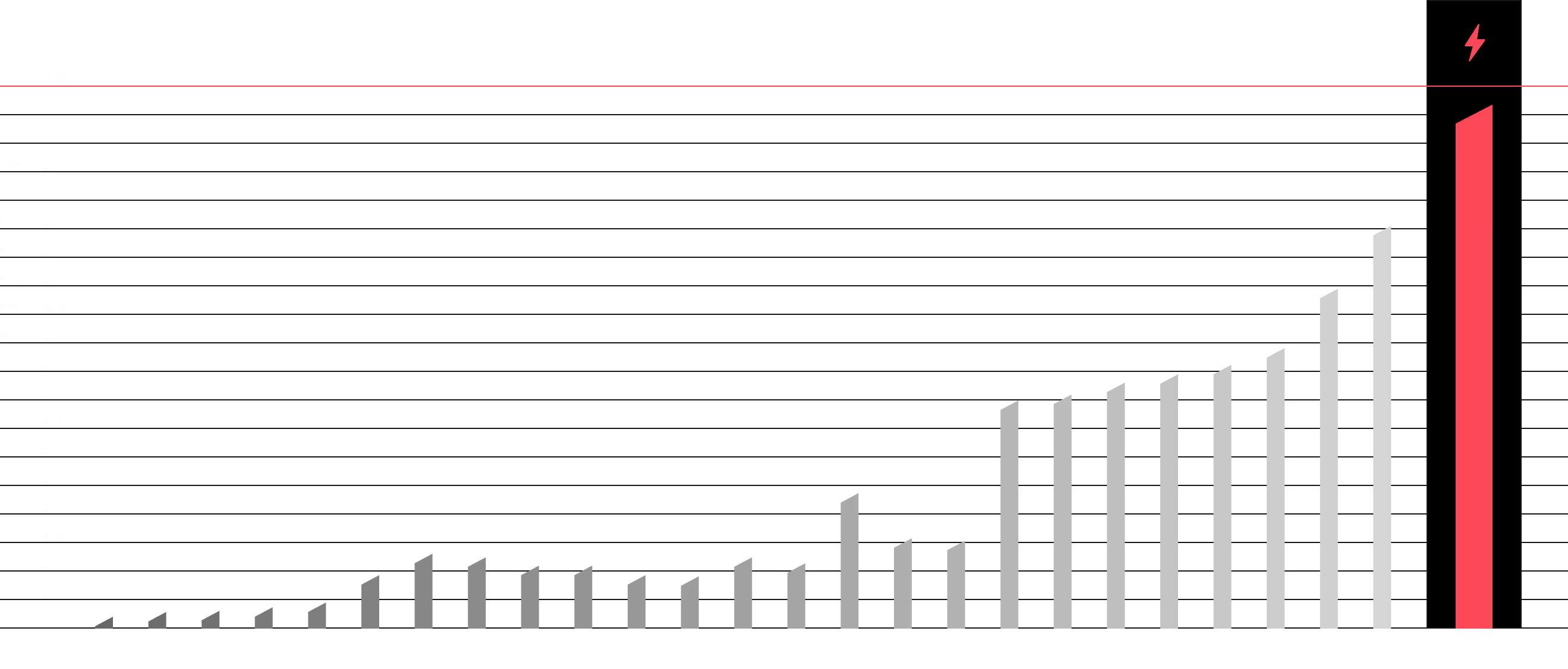
Large Language Models (LLMs) are revolutionizing business, but they also create a new, unprecedented attack surface. Our LLM Jailbreaking service is an advanced security test for your AI model. We find and neutralize the ways it can be manipulated to protect your reputation, data, and intellectual property before someone else does.
Overview