Red Team
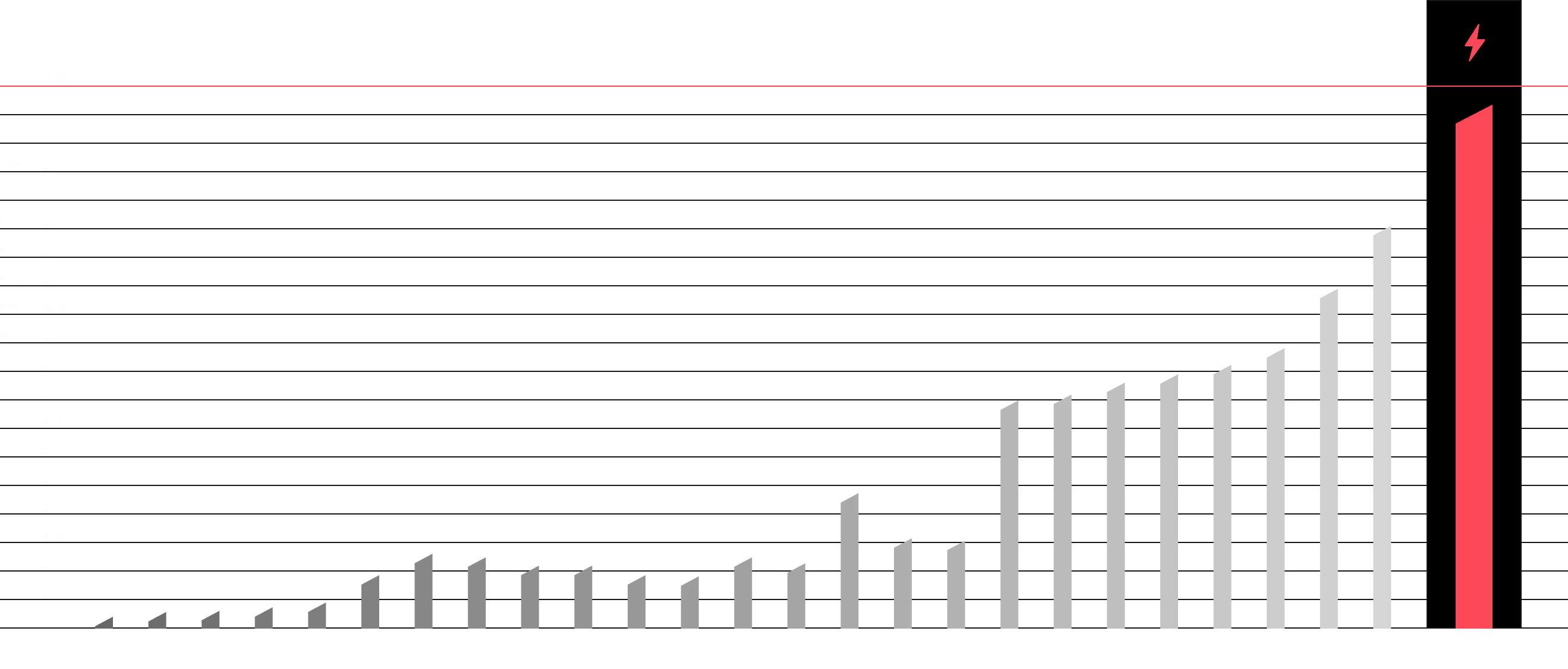
Red Team tests your defence strategy, not just your technology.
Penetration tests check the locks on the doors. Our Red Team service checks if the entire building can be robbed without leaving a trace. We simulate the actions of advanced persistent threats (APTs) to give you the only real answer to the question of how effective your security, people, and procedures are.
Overview